What is phishing?
The word phishing was first used in the mid-’90s by hackers stealing account information; the term came from an analogy from angling, as they would use lures, setting out hooks to “fish” for information from the “sea” of Internet users. While most users didn’t take the bait, a few did and Phishing was born!
Most of us have heard of Phishing, but we still get caught out so it’s worth reminding ourselves of all the different ways we could get hooked.
What is the most common example of phishing?
Typical phishing attacks come from scammers who send ‘dodgy’ emails to thousands of people, asking for personal information or containing links to rogue websites. Typically, the emails ask you to send money and take your details to sell or reuse to gain access to personal information. Some scammers have political or ideological motives and some aim to obtain business information.
Common examples of scams include:
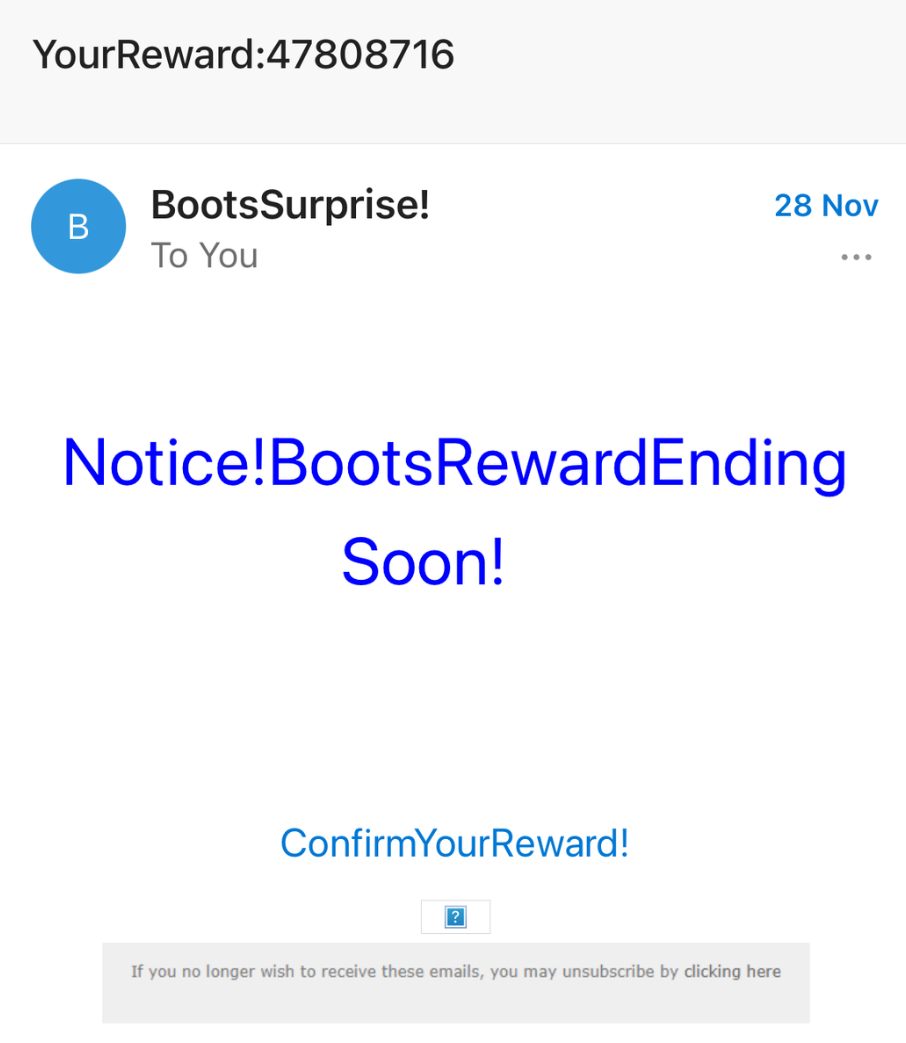
- Receiving ‘suspicious log-in attempt’ emails.
- Being informed there is a problem with your account information or payment details.
- Being asked to confirm personal or financial information.
- Requests to click on a link and make a payment.
- Offering free gift vouchers or rewards.
Is phishing malware?
At the end of the day, the scammer wants to extort money, harvest information for fraudulent use or gain a competitive advantage, and there are many ways they lure users into doing that. It can lead to malware or ransomware being installed on users’ systems and these can be used to damage and encrypt company information on servers leading to a very serious issue.
Phishing attacks are getting more difficult to spot, and some will still get past even the most observant users. So, given the prevalence of attacks, it’s almost certain that you will receive phishing attacks at some point.
How common are phishing attacks?
Phishing attacks are unfortunately quite common and occur frequently, which is why being aware of the common signs of phishing will help reduce the risk of an attack. The frequency of phishing attacks can vary depending on a range of factors including the current cybersecurity environment, the effectiveness of security measures and the popularity of targets.
Are phishing emails illegal?
Yes, under most jurisdictions phishing is seen as illegal as it involves identity theft, fraud, unauthorised access and violation of terms of service. Law enforcement agencies and cybersecurity organisations around the world work to identify and prosecute individuals or groups involved in phishing attacks.
Who is most at risk from phishing scams?
People who are less familiar with technology and cybersecurity practices are more likely to fall for phishing scams. This article covers everything you need to know about phishing, such as the different types, identifying scams, prevention and reporting attacks and helping to reduce your risk of an attack.
What are the different types of phishing?
Here are some pointers to help you identify the most common phishing attacks.
All these descriptions are very real methods used by criminals. It’s useful for everyone to have a good idea of the variety of approaches that inventive hackers have created to fool people. And new ideas are being created all the time, so don’t assume these are the only scams you will encounter.
- Phishing is a fraudulent attempt to obtain sensitive information or to entice a user to open a malicious file or website by a perpetrator disguised as a trustworthy entity in an electronic communication. It’s an example of social engineering techniques used to deceive users and is typically an email spoof instant messaging or text messaging.
- Spear Phishing is directed at specific individuals or companies and it differs from mass phishing in that attackers use personal information about their target to maximise their probability of success. Personal and company information is collected and reused in the attack that leverages friendship information from social networks. This type of attack has a very high success rate.
- Whaling is a sophisticated spear-phishing attack directed specifically at senior executives. It will often be presented as a legal document, tax form or some form of a high-profile complaint from a 3rd party organisation and they tend to be very subtle.
- Smishing & Vishing (Voice and SMS Phishing), where the phone is used instead of emails, Smishing involves criminals sending text messages (the content of which is much the same as with email phishing), and Vishing involves a telephone conversation. Frequently the scam involves a fake claim about a bank or credit card breach where the victim is asked to provide card details, transfer money or visit a bad website.
- Angler Phishing is a new method used by criminals that takes advantage of the information found on social media or to present fake and cloned websites. A mix of other methods is also incorporated, including posts, tweets and install messages and all are used to entice users to pass on sensitive information. Sometimes the information in users’ posts is gathered to create a Spear or Whaling attack.
- Catphishing (with a PH), is where a criminal gets to know someone closely to gain control over that person and then access information or resources.
- Catfishing (with an F), involves a person creating a social network presence as a fictional person to entice someone into a relationship where information is divulged or money extorted. This usually begins online, with the hope or promise of it progressing to real-life romance.
- Clone Phishing, with this type of attack an earlier email with a link or attachment is being copied and resent from a spoofed email address with a malicious file or link. This typically requires the sender or recipient to have been previously hacked.
- Tabnabbing relies on the fact that the user no longer remembers that a certain browser tab was the result of a link unrelated to the login page because the fake login page is loaded in one of the long-lived open tabs in their browser. It relies on the ability of browsers to navigate across a page’s origin in inactive tabs a long time after the page is loaded.
- Pharming, with this type of attack users, are sent to a fraudulent website that appears to be legitimate. This is achieved by the criminal changing the hosts’ file or poisoning the DNS settings on a victim’s poorly protected computer which can be a home computer, rather than a corporate business server.
How to identify phishing emails
It’s hard to be specific, but phishing emails are generally ‘of a type’, with similar characteristics, so look for the following warning signs:
- Poor grammar and punctuation - Many phishing scams originate overseas and often the spelling, grammar and punctuation are poor. Others will try to create official-looking emails by including logos and graphics. Is the design (and quality) what you’d expect from a large organisation?
- Address - Is it addressed to you by name, or does it refer to ‘valued customer’, or ‘friend’, or ‘colleague’? This can be a sign that the sender does not know you, and that it is part of a phishing scam.
- Sense of urgency? -Does the email contain a veiled threat that asks you to act urgently? Be suspicious of words like ‘send these details within 24 hours’ or ‘you have been a victim of crime, click here immediately’.
- Where has it come from? - Look out for emails that appear to come from a high-ranking person within your organisation, requesting payment to be made to a particular bank account. Look at the sender’s name – does it sound legitimate, or is it trying to mimic someone you know? If it sounds too good to be true, it probably is. It’s most unlikely that someone will want to give you money or give you access to some secret part of the Internet.
Protective measures
Train your Staff Members:
- Understand the risks - Take some time out with your staff and management team and discuss the ways that a hacker could target your business. Make sure everyone understands the risks of Malware and how to identify suspicious emails.
- User training - Conduct user training and make sure they understand the ways you expect interactions with other businesses to operate and behave so that they’re better equipped to spot strange requests such as an invoice for a service that you haven’t used.
- Encourage users to question suspicious and unusual requests – even if they appear to be from important individuals. Make sure that just because the name on an email is set to be “Head Honcho” and flagged as VERY URGENT does not make it genuine.
- Make sure that your staff are encouraged to ask for help if they think that they might have been a victim of phishing, especially if they’ve not raised it before. It’s important to take steps to scan for malware and change passwords as soon as possible if you suspect a successful attack has occurred.
- Do not punish staff if they get caught out. It discourages people from reporting in future and can make them so fearful that they spend excessive time and energy scrutinising every single email they receive. Both these things cause more harm to your business in the long run.
- Help your staff understand how sharing their personal information can affect them and your organisation. This is not about expecting people to remove all traces of themselves from the Internet. Instead, support them as they manage their digital footprint, shaping their profile so that it works for them and the organisation.
Set Passwords and User Permissions:
- You must implement the principle of “Least Privilege”, this means giving users the lowest level of permission required to use their systems and work effectively, so if they are the victim of an attack, the potential damage is reduced.
- Insist on two-factor authentication (2FA) on all accounts that have it available – especially email so that even if an attacker knows your passwords, they still won’t be able to gain access.
Additional Steps:
- Set up external email filtering & scanning
- Why not tell your suppliers and customers that ‘we never ask for your password’, or ‘our bank details will not change at any point’ so that a culture of care is engendered?
What are the phishing risks to companies?
Attackers use publicly available information about your organisation and staff to make their phishing messages more convincing. This is often gleaned from your website and social media accounts (information known as a ‘digital footprint’). Understand the impact of information shared on your organisation’s website and social media pages. What do visitors to your website need to know, and what detail is unnecessary (but could be useful for attackers)?
What to do if you click on a phishing link?
If you find yourself in a position where you have clicked on a phishing link, immediately follow your incident response plan created by your organisation. If you don't have a plan, then key steps are likely to include the following:
- Raise the alarm - start by reporting to your manager and those responsible for IT security.
- Consider setting up a response panel.
- Contact a security expert - If you have an expert security contact, follow their instructions. Tell them as much as you can about what happened and any recent history that, with hindsight, might be relevant.
- Alert contacts - bear in mind your account might be hijacked, so the message will need to be handled by another individual. If you have contacts handling client messaging, they should be involved in managing this aspect.
- If possible, revoke all active sessions for the victim.
- Reset credentials - Go through a process of resetting credentials (username and password) - for at least the known victim.
- Clear all 2FA methods and have the victim recreate them.
- If the same credentials have been used on other websites, reset those credentials too.
- Scan device - Run a scan on the affected device, and consider isolating it until shown to be clear.
- Check your email account - If the account can send and receive email, check mail logs and rules, check send items for sent emails, and check any automation or message handling rules.
- Check through any available logs and look for unauthorised logins or activity on the account and other accounts. You may need to go through and clear your account history and cache. It may be an idea to go through the same account recovery process for any other accounts that may also have suspicious activity.
After the fallout is dealt with, review the process and adapt the incident response plan. If you don't have a plan, create one - we can assist with this.
How to report a phishing attack?
Be aware of what your partners, contractors and suppliers give away about your organisation online. If you believe that your organisation has been the victim of online fraud, scams or extortion, you should report this through the Action Fraud website. Action Fraud is the UK’s national fraud and cybercrime reporting centre. If you are in Scotland contact Police Scotland on 101.
The National Cyber Security Centre (NCSC) provides an excellent platform for reporting scams. You can confidently forward numerous suspicious messages to them, and they will investigate and work towards identifying and removing the scams.
Report a scam email: https://www.ncsc.gov.uk/collection/phishing-scams/report-scam-email
Report a scam text message: https://www.ncsc.gov.uk/collection/phishing-scams/report-scam-text-message
Report a spam phone call: https://www.ncsc.gov.uk/collection/phishing-scams/report-scam-call
Report a scam website: https://www.ncsc.gov.uk/collection/phishing-scams/report-scam-website
Report a scam advert: https://www.ncsc.gov.uk/collection/phishing-scams/report-scam-advert
What to do if you have shared personal information: https://www.ncsc.gov.uk/collection/phishing-scams/what-to-do
